Workflow is less work and more flow
Simplify all record keeping, communication, scheduling and information sharing; especially when mobile.
Automate work, improve consistency.
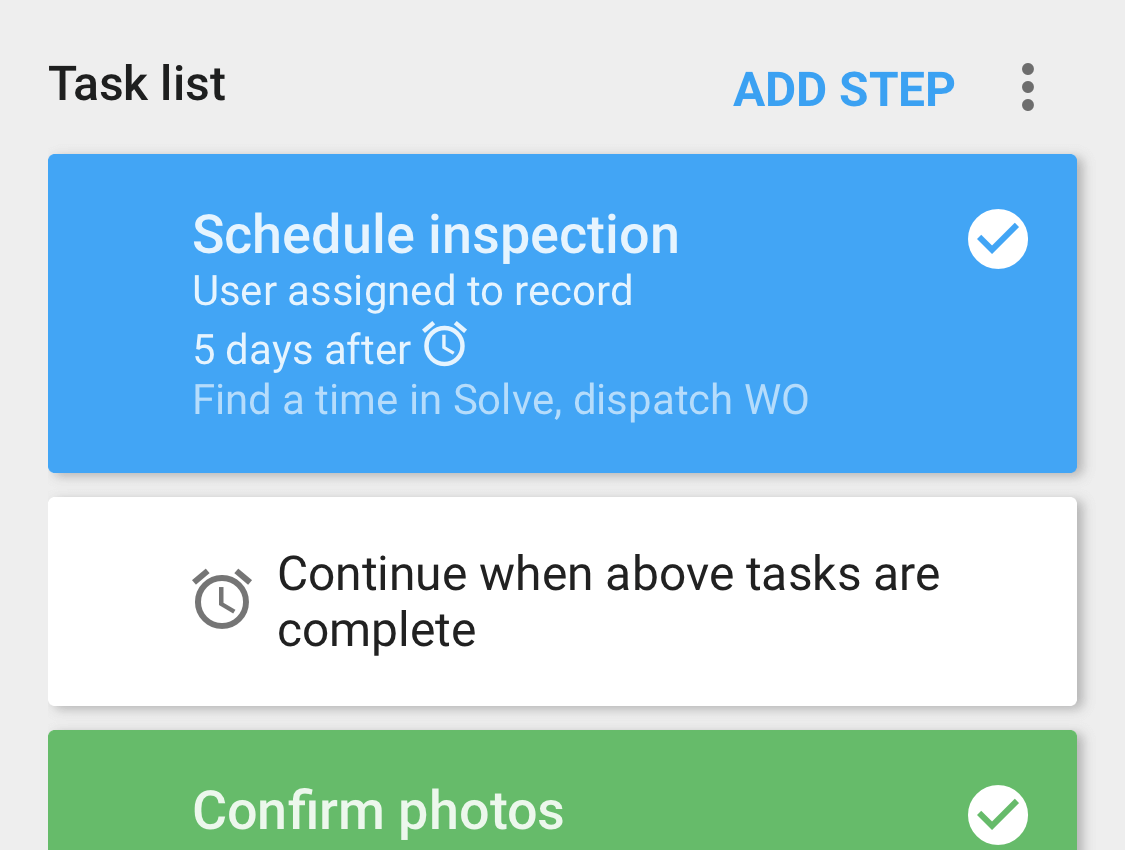
- Streamline routines with multi-step workflows
- Tap to effectively hand-off work with all relevant details; tracked to completion
Centralized data pays off big time
Move away from paper, spreadsheets, excessive calling, and unloved software.
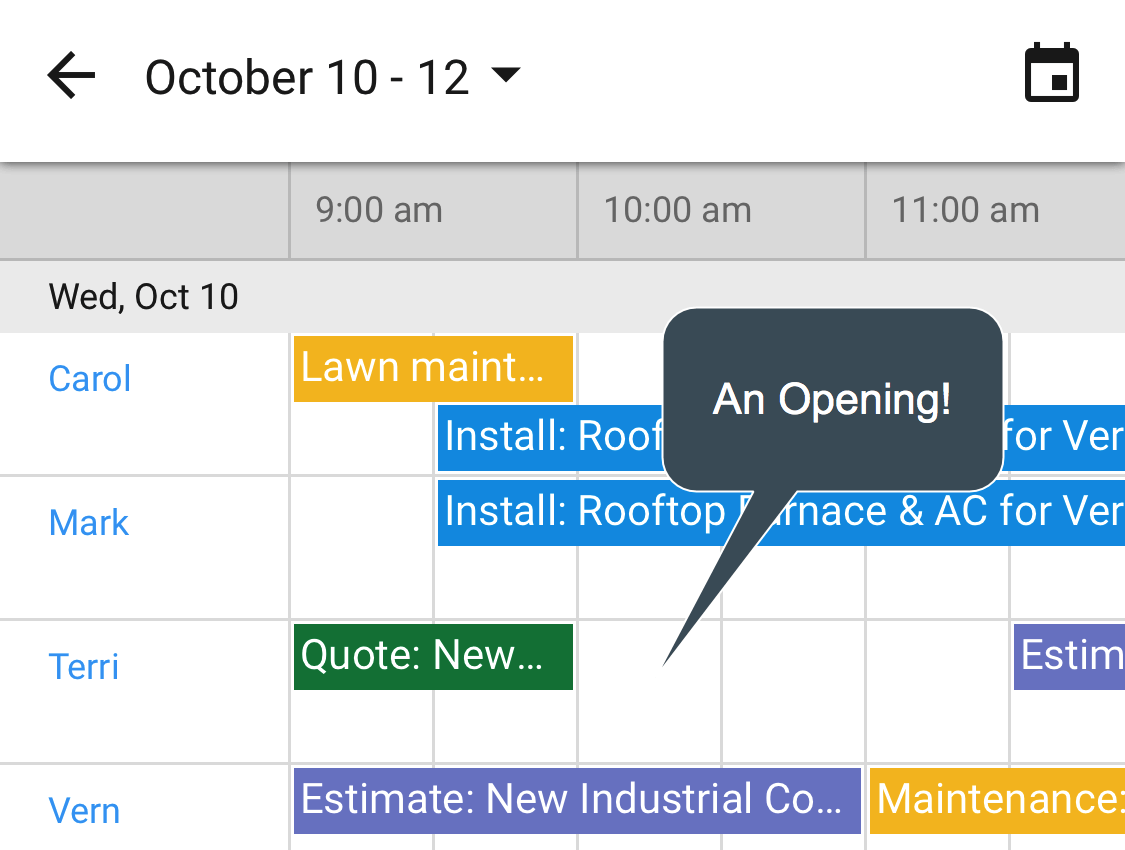
Visualize and schedule activity across multiple resources.
- Centralize Google Calendar and Google email history across the entire domain
- Customize to capture the right info, then leverage it with renowned search and flexible Report Builder
Your team earns more 5-star reviews
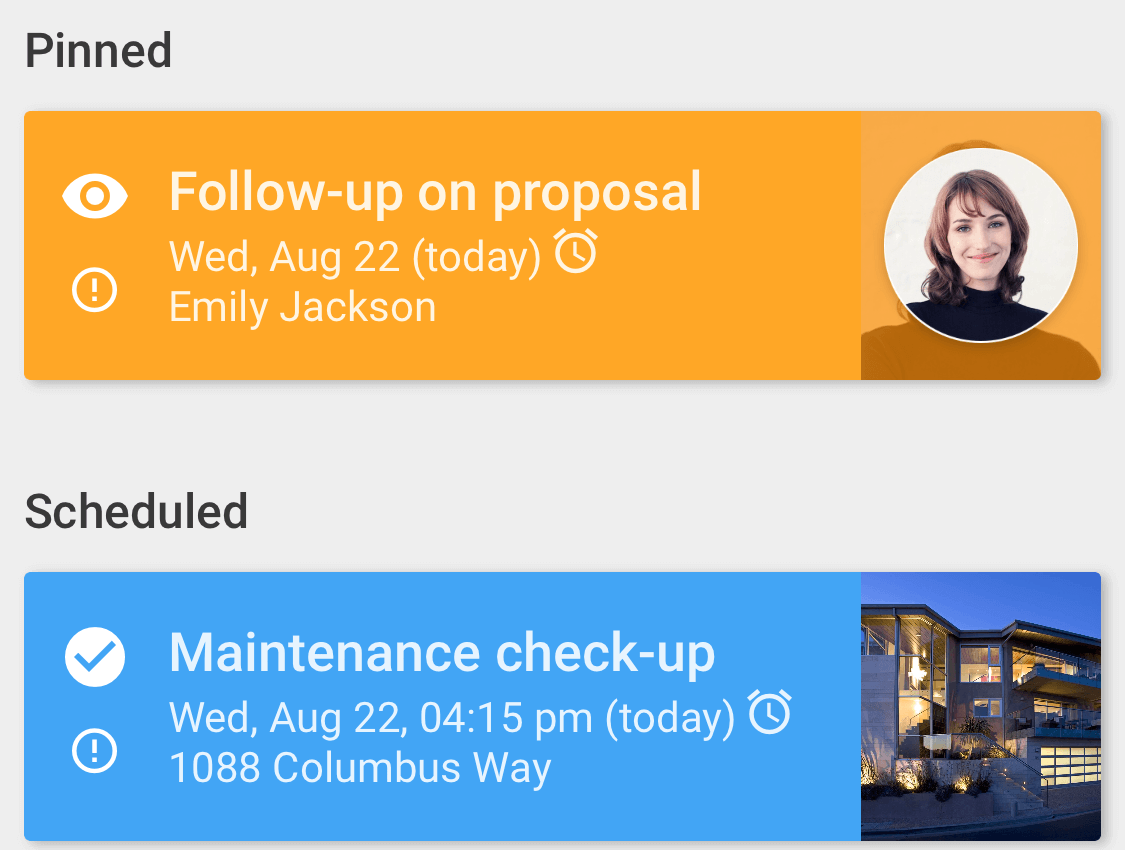
Automatically remind staff when to act and highlights what the priorities are.
Make it drastically easier for all staff types to contribute, improve service and offer proactive support.
- A simple, self-managing personal dashboard highlight what to focus on
- Exceptional mobile apps ensure everyone has the information they need, even if their workflow is focussed primarily around Google Calendar